APPLICATION UNDERSTANDING FOR JAVA (AU4J)
Legacy applications are useful systems built with old, unknown, or outdated technology. They are expensive to replace, their services meet expectations, but their use poses several problems.
Since the 1980s, Legacy applications have been a serious problem in the field of Information Technology. A decade ago, everyone thought of the word “Legacy” in systems written in outdated languages like COBOL, Software AG’s Natural language, or IBM’s RPG language.
In the last ten years, however, mainstream technology has changed dramatically, and this has affected the Java community as well. The cloud rendered some aspects of Java EE unusable, so much so that it eventually removed Java EE from Oracle’s Java portfolio. Microservices replace monolithic servers installed in heavy-duty containers.
In the software industry, in the case of brownfield development, the goal is to maintain and further develop an old code base.
The problem here is often not the complexity of the new functions or the complexity of the environment, but the need for a detailed and thorough understanding of the operating system, both in business and IT terms. Sometimes this understanding is incomplete in both senses. Experts in the field and authors of the original code would be needed, but they are only available to a limited extent or not at all.
Application Understanding for Java (AU4J) is an application designed to solve the above problem.
Application Understanding for Java development
The AU4J methods and algorithms created by our company, ENTIS-NET Ltd., rely on similar applications already developed for the COBOL, RPG and Natural programming languages, and implements our existing application understanding technology and accumulated knowledge for the Java programming language.
However, this goal included several new challenges as we applied the method to object-oriented language for the first time.
Whatever the goal with the old code, whether it’s rewriting from scratch, continuing the brownfield development, or just deciding between the above two options, you need to understand the business logic embodied in the application. However, extracting business logic from an existing code base is not an easy task. Developers have to examine hundreds of thousands or even millions of lines of code.
Today, there are several excellent tools available to support code mapping and decryption. These usually follow the control structure of the program, from top to bottom from the entry point along a directed graph of control flow.
However, traversing the control structure is difficult to follow, with this approach the system becomes complicated and opaque in a short time because the complexity increases exponentially along the way.
In contrast, Application Understanding for Java (AU4J) takes a completely different, new approach to extracting business logic from application code.
The method of understanding the AU4J application follows the opposite direction. Recognizes the points in the code where persistent data is generated (output endpoints). From here, the traversal of the graph moves backwards, collecting the code snippets that are involved in creating the constant data.
The result is pure business logic, omitting all other aspects of the architecture, such as logging and management functions.
As a process, extracting business rules is somehow similar to angiography, a medical imaging method used to visualize blood vessels. The developer injects paint into one or more endpoints of the system and looks at what has stained.
The AU4J tool can be integrated with an IDE (currently the plugin was developed for JetBrains IntelliJ IDEA environment), so developers can process AU4J result lists in their own familiar environment.
In addition to extracting business rules, the AU4J web app offers several other tools to support application maintenance and brownfield development.
Functions of Application Understanding for Java (AU4J)
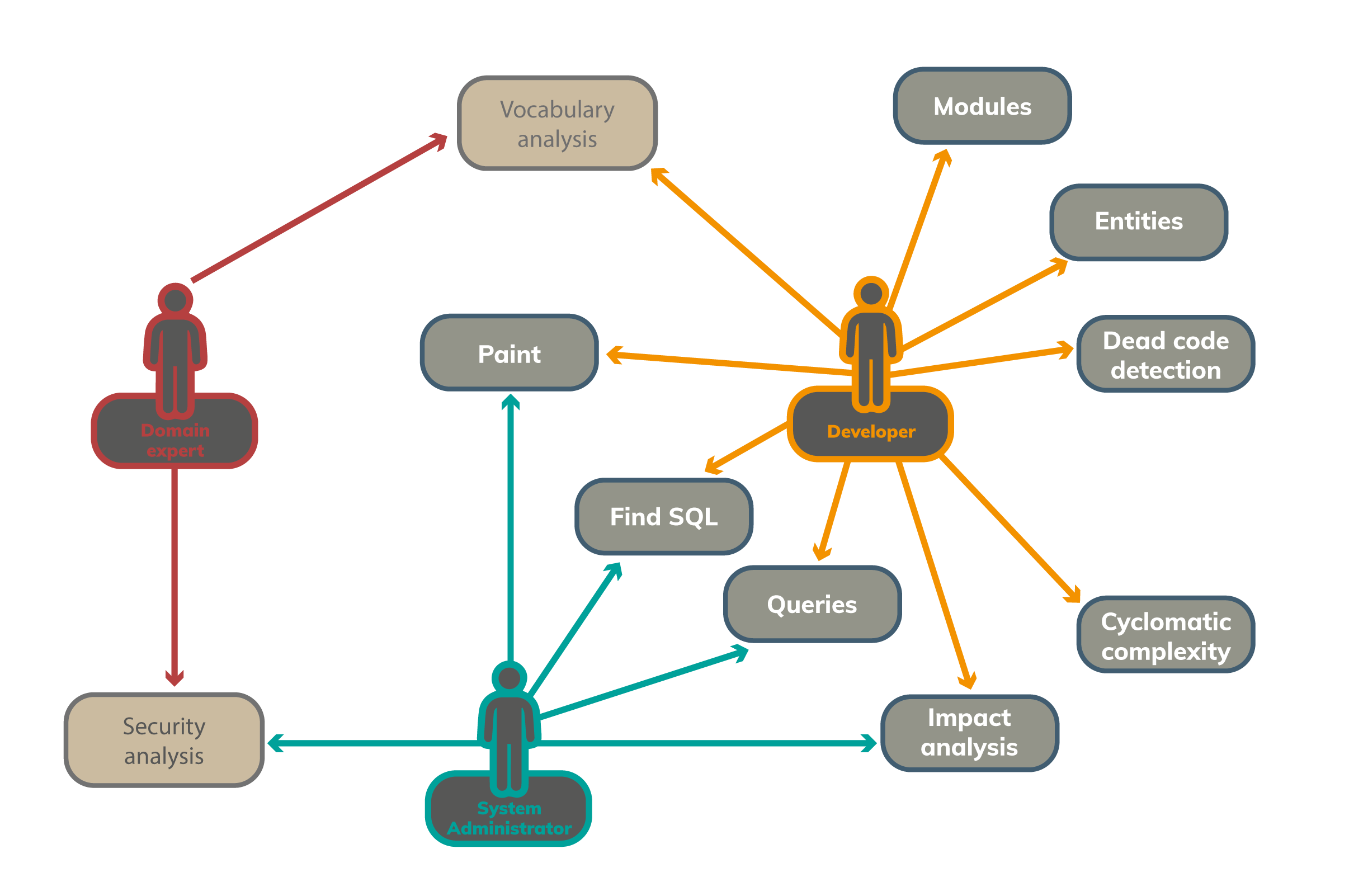
Scan
Scan, comprehensively examine and analyze the application based on the source code.
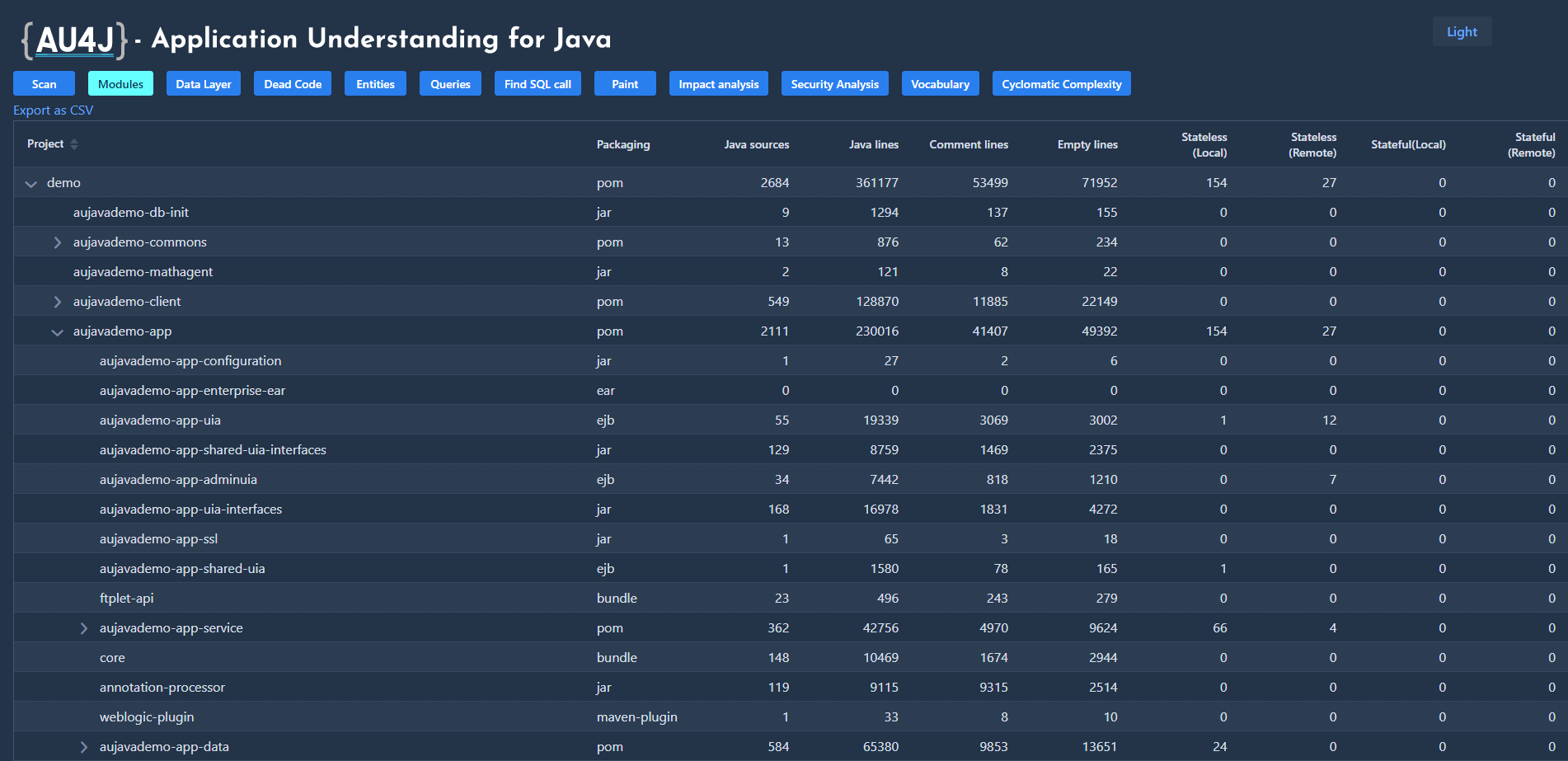
Modules (Module Hierarchy)
After analysis, displays the hierarchy of application modules as an expandable tree. It also displays module statistics.
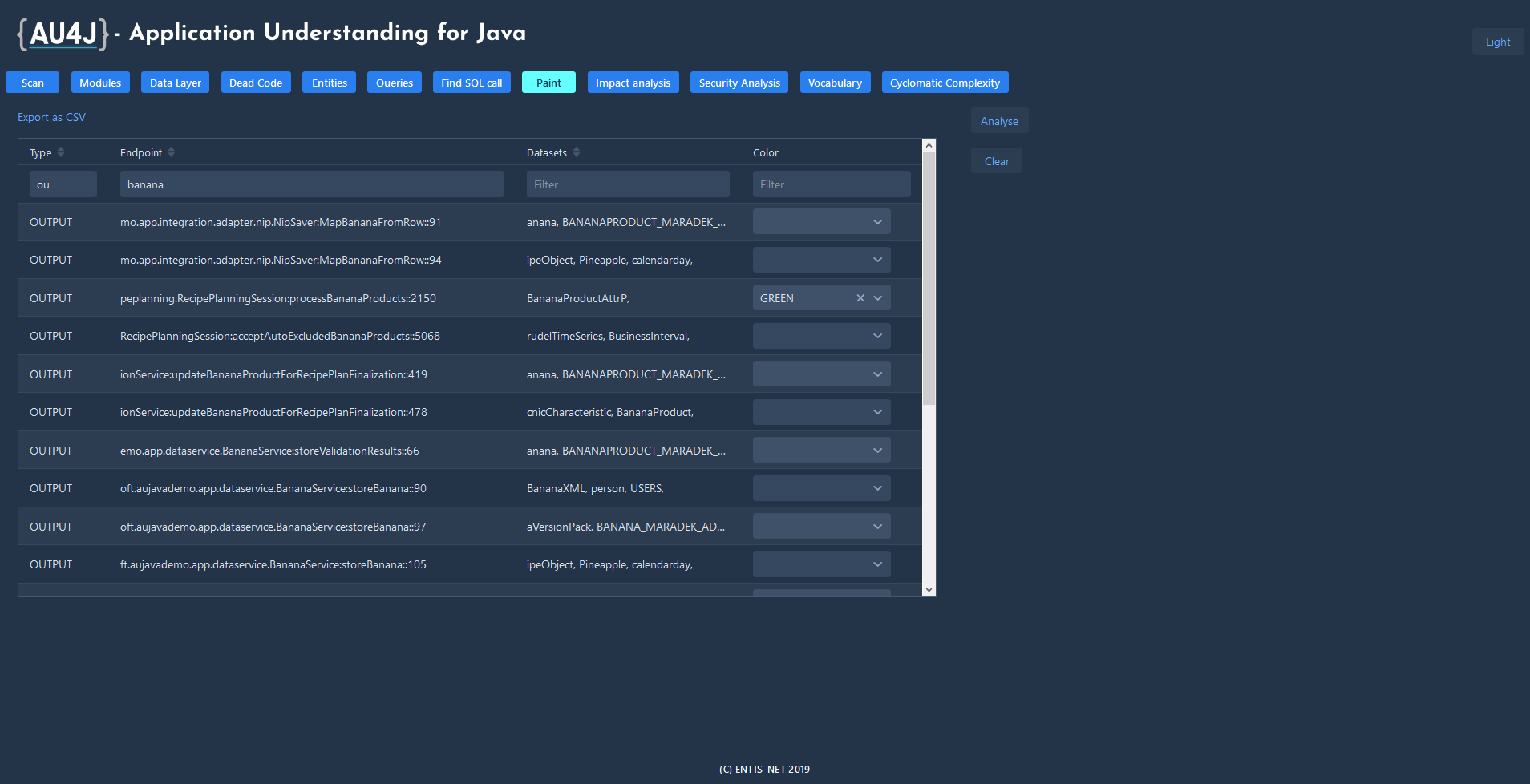
Paint
Expands the business logic by listing the codes and data files associated with the selected endpoints. For an output endpoint (in a selected color), it paints the codes that are involved in its production, and for an input endpoint, those that are involved in its processing.
Dead Code
Detects unused code snippets in the application. The recursive algorithm also filters out codes that are only called by unused portions of code.
Invocation Map
For all methods in the application under test, it lists all the codes that call that method.
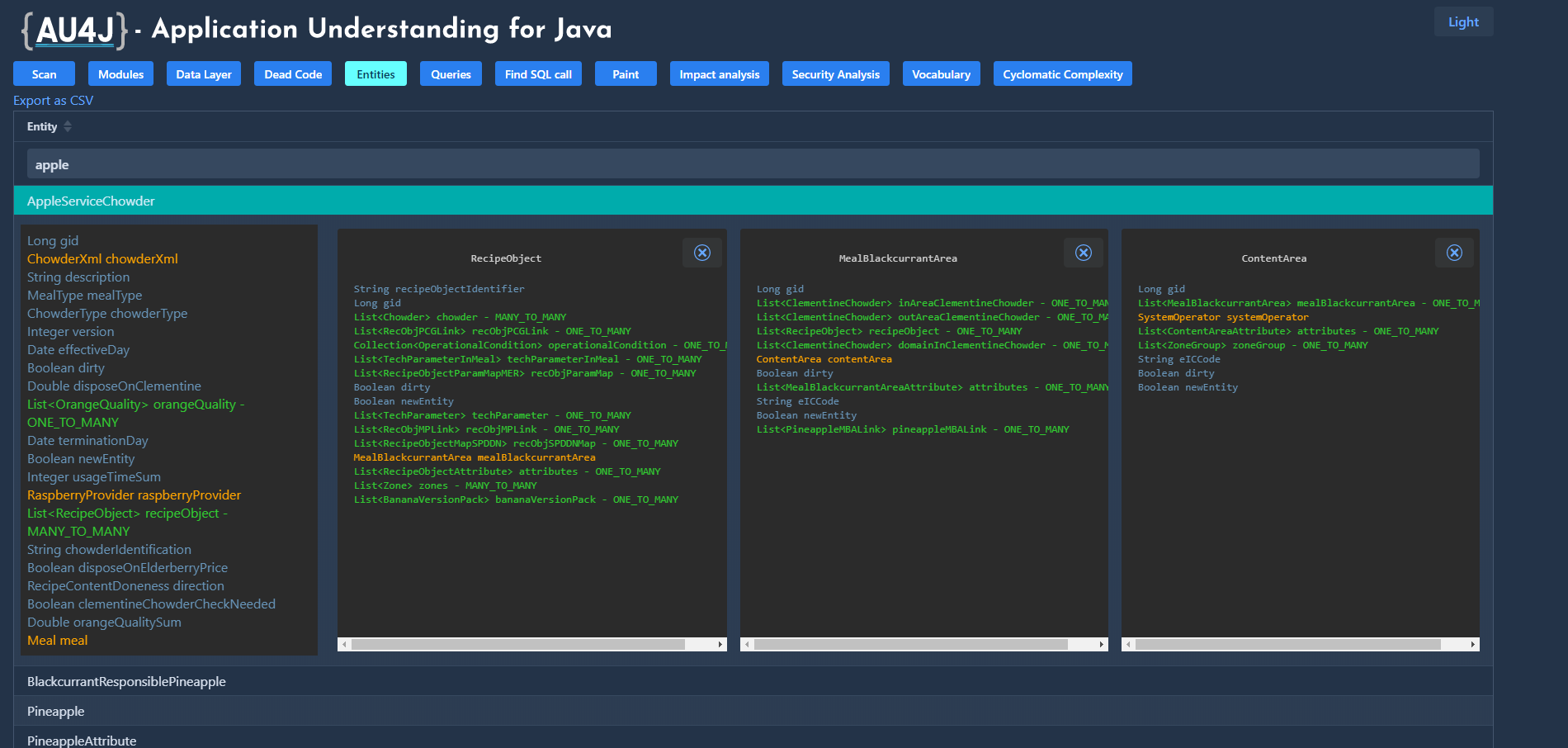
Entities
Lists persistent entities in the application. If a property is a reference to another entity, it also shows its structure when clicked, so that it can display entire reference chains at once.
CYCLOMATIC COMPLEXITY
Displays the total and average complexity of the elements of the module - class - method hierarchy. The tool helps with resource planning for testing and points out methods that are difficult to maintain in code.
Queries
Lists named, native and inline queries in the code. Click to display the formatted source of the query in both JPQL and SQL.
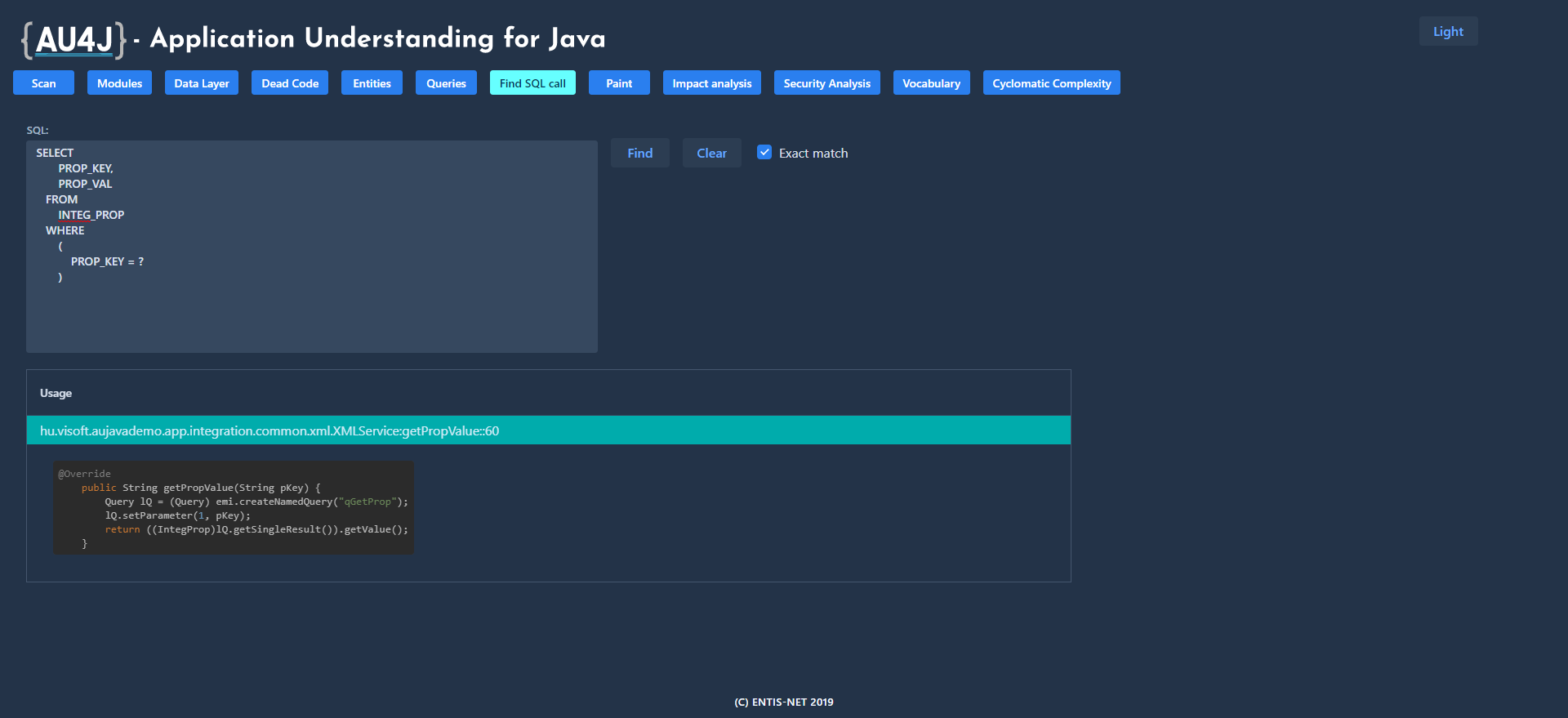
SQL Finder
It is a common requirement on the part of operators to find the source of an SQL statement read from the log in the application. This function identifies the lines of code that could have started the specified SQL or JPQL query.
Impact analysis
The AU4J is connected to the version control software that stores the source code. After modifying the source code, if the user enters a commit ID, the application returns a list of changed user and interface functions. The tool reduces the resource requirements for regression testing and allows you to assess the security impact of a change.
Vocabulary analysis
Collects words used as names in the application (including components of compound names), which allows you to group application concepts. It shows all the uses of a given word, helping to unify the language of the system, develop a common vocabulary between domain experts and developers, and allow synonyms to be paired (in mixed language codes).
Security analysis
The business expert can assign damage value to the data files and tables. The device handles damage caused by data leakage and data breach separately. The AU4J displays these at entry points, in other words, it shows quantitatively how critical each entry point is from security perspective.
Who is the application for
Application Understanding for Java is both a useful tool
- IT specialists operating the system,
- software developers and system administrators providing support (system support),
- professionals planning to improve or modify the system, and
- for business professional users of the system.
It can uniquely show that a monolithic application
- how it can be broken down into individual modules or even micro-services;
- what dead codes (unused codes) it contains
- examines the impact of a modification (repair or new development) on safety and which use cases are sufficient to test instead of the full regression test;
- significantly speeds up the identification of the cause of operational errors
- is able to classify the entry points of the application based on the extent of the damage that can be caused through them, how critical each entry point is from a security point of view.
The project was implemented within the framework of the support of the innovation activities of micro and small enterprises, on 2018-1.1.1-MKI-2018-00148. We have been continuously developing the product ever since.
October 7, 2020